How to Keep Your Company Safer from Cyberattacks
The manufacturing sector continues to be a top target for cyberattacks — right up there with financial services and healthcare companies. Half of manufacturing companies have fallen victim to at least one data breach in the last year.
Digital transformation is enabling manufacturing companies to become more efficient and effective. It’s helping them thrive in an increasingly complex and fast-paced world. As more employees are using digital tools for day-to-day business processes, however, leadership teams must take responsibility for creating a culture of awareness around IT security.
It’s IT’s job to set up, configure and manage cybersecurity — but it’s everyone’s job to maintain it.
Effective cybersecurity requires IT to be in partnership with the business people, and the executive team needs to keep this conversation going. In this article, you’ll learn why this is important to your company, what can happen when this conversation falters, and what it looks like to succeed.
Why Cybersecurity Is Increasingly Important in Manufacturing
A cyberattack doesn’t just impact your company, it impacts your employees and customers, too. Security breaches can kill productivity, corrupt data, cost the company financially — or even shut down entire facilities.
A recent report from Verizon found that the majority of attacks on manufacturing companies are financially motivated, but espionage is a significant motivator as well. Another major concern is disgruntled employees making off with data.
In that report, ransomware was not considered a “breach,” per se, but it was still noted as a clear and present danger. In fact, ransomware was found in 23% of all malware incidents.
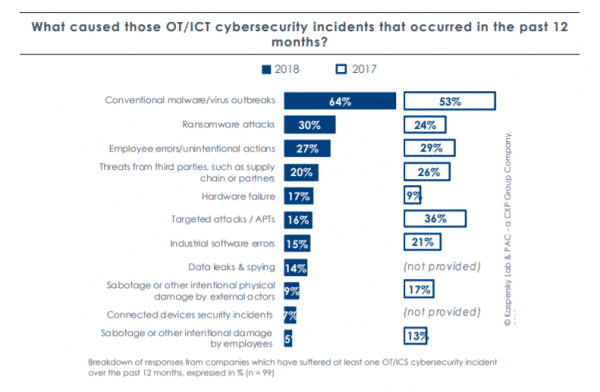
As you can see from The State of Industrial Cybersecurity white paper from CXP Group, threats shift from year to year. The important takeaway here is that we can never rest on our laurels when it comes to IT security. Keeping awareness high and best practices sharp is critical to keeping your company safe from cybercriminals.
Most threats come through email
One trend that continues to increase is threats being sent through email. That same Verizon report found that 90% of malware is delivered via email, in fact. All it takes is one wrong click, or one innocent email forward for entire systems to be corrupted.
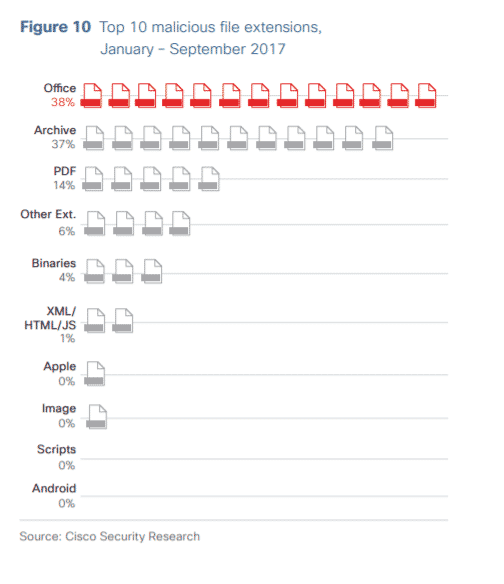
The scary thing is, malware sent through email can look completely innocent. Cisco found that the most common malicious file extensions came from Microsoft Office programs — Word, PowerPoint and Excel — which most of us use almost every day.
Phishing scams continue to evolve as criminals become more cunning. “Spear phishing” is an attack through an innocent-looking email that seeks to steal sensitive company information or access a company’s network.
We experienced an email incident recently at Syte, in fact. I was sent an email that looked legitimate, and if I hadn’t taken a moment to give it some extra scrutiny, I might have forwarded it on — which would have triggered the embedded malware and caused a cascade of forwards to all my contacts, putting my entire network at risk.
Creating a Culture of Awareness
Your IT team probably takes cybersecurity very seriously. But the reality is:
You and your employees are your company’s first line of defense.
Consistent and mandatory cybersecurity training is the best thing you can do to create and maintain a culture of awareness that keeps criminals at bay.
Because business users are responsible for the majority of the digital traffic coming in and out of your company, your IT people need their help in the fight for IT security.
Make cybersecurity policies and procedures part of your employee onboarding process. Include them in your Employee Handbook.
Keep all employees informed on cybersecurity threats with regular training and updates. Scams and attacks evolve and change, and everyone needs to remain aware of what to look for — especially in their inboxes.
Make password hygiene mandatory. Employees should immediately change default passwords and make it a habit to change all passwords regularly.
What It Looks Like to Win the Cybersecurity War
When a cyberattack happens — and it will — a culture of awareness is your best bet to combat it.
This story on the National Institute of Standards and Technology blog is a great example of how employee awareness works to protect your company. Here’s a quick recap:
An employee in the accounting department of a small-to-medium-sized manufacturing company received an email that appeared to come from a known supplier. The attacker tailored the email to look as genuine as possible, and embedded malicious code in the attached PDF. When the employee opened the PDF, the malware was introduced into the company’s network.
The company had trained all their employees to recognize and respond to phishing attacks, however. As soon as the company detected the threat, all the employees knew what they were supposed to do. The IT team was able to act quickly and remove the infected computer from the network, which stopped the malware in its tracks.
Your IT team might be the experts in battling cybercriminals, but everyone — from executive leadership to individual contributors — has a role to play in keeping your company safe.
IT teams have a lot on their plate at family-owned manufacturing companies. Read this article and learn how not to overwhelm them with your growth strategy.
ERP Readiness Self-Assessment
Is your organization ready for a new or upgraded ERP solution? Find out with this complimentary self-assessment.
Doing Business Better
You strive for excellence, believe in your people, and want to do things right the first time. And you know that you need help to get to the heart of your business challenges and make the best choices for the future of your privately held manufacturing and distribution company. That’s where we come in.
We help you focus and find exactly the right path to accelerated growth and sustainable success — from your people to your processes to your ERP software.